Table of Contents
ToggleImagine a world where hospitals, transportation, and power systems stop working because of computer attacks. It’s not a made-up story; it’s really happening in the age of cyber attacks.
These attacks are not just done by kids in their basements. Now, we see more serious attacks from countries or people who want money. They can mess up important systems, steal secret information, and cause a lot of problems.
The attacks are getting smarter. They use fancy tools, like artificial intelligence, to find weaknesses in computer systems. They can even make viruses that spread on their own and attack many things at once.
BUT FIRST THINGS FIRST. What is the meaning of cyber resilience?
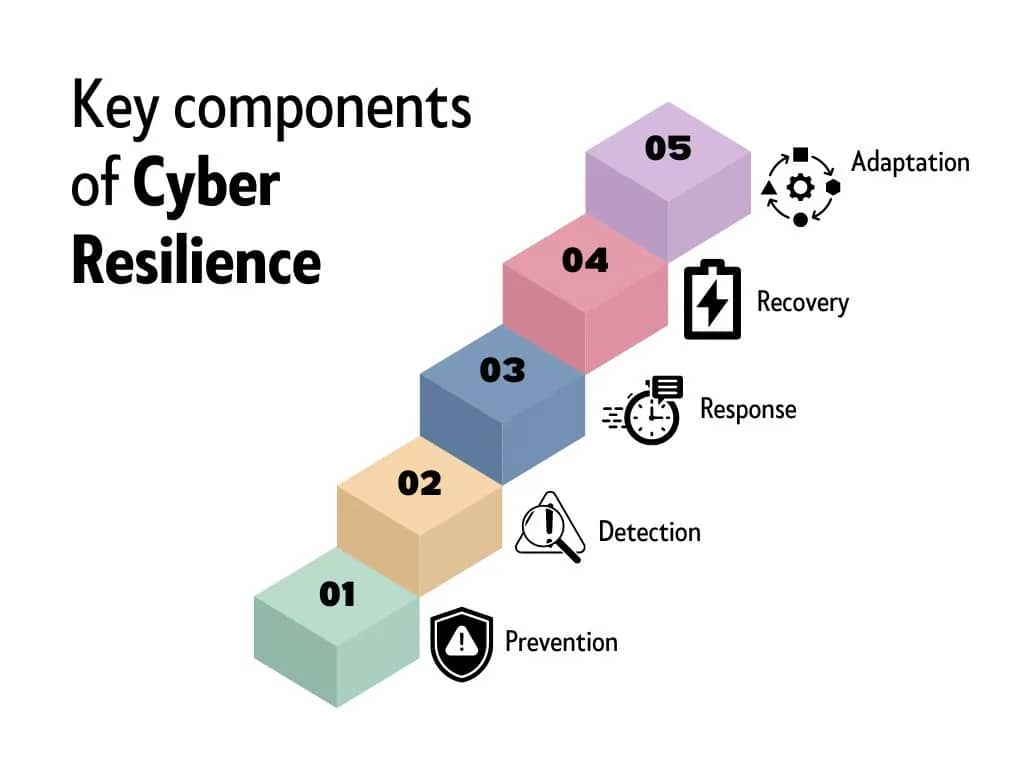
Cyber resilience refers to an organization’s ability to anticipate, prepare for, respond to, and recover from cyber attacks or security incidents. It involves a comprehensive and proactive approach to managing and mitigating the impact of cyber threats, focusing not only on preventing attacks but also on ensuring that operations can continue smoothly even in the face of a successful breach.
In our increasingly interconnected and digitized world, where cyber threats are ever-present, the concept of “cyber resilience” emerges as a critical and proactive approach to staying safe in the digital environment. Cyber resilience goes beyond traditional cybersecurity measures, emphasizing the ability not only to withstand and prevent cyber attacks but also to adapt, respond, and recover swiftly when breaches occur.
CYBER HYGIENE-
First of all, what is cyber hygiene?
Think of cyber hygiene like taking care of your computer’s health, just as you take care of yourself. You know how you wash your hands, take showers, and stay clean to stay healthy? Well, cyber hygiene is like doing the same for your computer.
Imagine your computer as your house. Cyber hygiene is the routine you follow to keep it clean and secure. It involves simple things like creating strong and unique passwords, being careful about what you click on the internet (just like you’re careful about touching things that might be dirty), and making sure your computer gets the latest updates (kind of like getting vaccines for your health).
In everyday terms, cyber hygiene is about forming good habits to keep you and your computer safe in the online world. It’s like cleaning your house to prevent problems – you keep your computer clean and healthy to prevent cyber issues. So, just as you look after yourself, it’s important to look after your computer too!
“In the digital world, just as we care for our health to prevent illness, practicing cyber hygiene is the key to resilience against evolving online threats.”
We have literally come out with a A Dictionary of Cyber Terms, to break this down for you.
Phishing-
Phishing is like tricking someone into sharing sensitive information. It’s like a fake email or message pretending to be from a trustworthy source, trying to get you to give away your personal details.
Malware-
Malware is like a digital troublemaker. It’s a software designed to cause harm to your computer or steal information. Viruses, spyware, and ransomware are all types of malware.
Zero-Day Attacks-
Zero-day attacks are like surprise attacks. They happen when bad guys find and use a weakness in a computer system before the good guys (software makers) even know it exists. It’s like opening a secret door before the owner realizes there’s a problem.
Vulnerability Assessments-
Vulnerability assessments are like security check-ups for your computer. It’s when experts look for weak spots in your system that hackers could exploit. They find these vulnerabilities before the bad guys do, so you can fix them and stay safe.
Firewall-
A firewall is like a security guard for your computer. It’s a barrier that keeps out unwanted stuff from the internet, like viruses and hackers. Imagine it as a protective wall around your digital space.
- Encryption-
Encryption is like turning your message into a secret code. It makes your information unreadable to anyone who doesn’t have the “key.” It’s like sending a letter in a language only you and the recipient understand.
- Two-Factor Authentication (2FA)-
Two-factor authentication is like having two locks on your door. To access your account, you need not just a password but also another code, often sent to your phone. It adds an extra layer of security.
- DDoS (Distributed Denial of Service) Attack-
A DDoS attack is like a traffic jam on the internet. It overwhelms a website with too much traffic, making it slow or unavailable. It’s like having so many cars on the road that no one can move.
- Social Engineering-
Social engineering is like tricking people in person. Instead of attacking the computer, hackers manipulate individuals to reveal confidential information. It’s like someone pretending to be a friend to get your secrets.
- Patch-
A patch is like fixing a hole in your favorite sweater. It’s a small piece of code that updates or repairs your software, closing any security gaps. It’s essential to keep your digital ‘clothes’ in good shape.
LET’S NOW TALK ABOUT THE ACTUAL SCARY BEAST ATTACKS.
“Staying safe online is like securing your home – strong habits, locks, and a watchful eye keep you protected against the beasts of the cyber world.”
Don’t worry though, apart from telling you truthfully how harmful they’re, we’ve come up with the actionable simple tips for you too!
Practical Steps for Cyber Resilience
FOR INDIVIDUALS-
Secure Home Network and Devices-
-
- Set a strong Wi-Fi password.
- Update your devices regularly.
Good Password Habits-
-
- Use unique passwords for accounts.
- Enable two-factor authentication.
Stay Informed-
-
- Keep an eye on security updates.
- Be cautious about new online threats.
Consider Cyber Insurance-
-
- Explore insurance options for extra protection.
- Understand what’s covered in case of a cyber incident.
FOR BUSINESSES-
Cybersecurity Policy-
-
- Develop clear rules for online security.
- Communicate policies to all employees.
Employee Training-
-
- Educate staff on cyber risks.
- Teach best practices for security.
Access Controls and Encryption-
-
- Limit who can access sensitive data.
- Encrypt important information.
Regular Assessments-
-
- Check for vulnerabilities in systems.
- Test defenses with penetration testing.
Incident Response Plan-
-
- Have a plan for cyber emergencies.
- Ensure employees know what to do.
Here below are some thrilling updates to keep your adrenaline pumping-
Zero-Day Exploits in the Wild-
- Log4Shell– This critical vulnerability in the ubiquitous Apache Log4j logging library sent shockwaves in December 2021. Hackers wasted no time, exploiting it to target servers worldwide, including NASA and Minecraft. Thankfully, patches were quickly deployed, but the incident highlighted the potential devastation of zero-day vulnerabilities.
Ransomware Rampage-
- REvil’s Demise- This notorious ransomware gang, responsible for crippling attacks like Kaseya VSA, announced its shutdown in July 2022. While some speculate it’s a tactical retreat, others believe it reflects internal conflicts or law enforcement pressure. Nevertheless, the threat landscape remains dynamic, with other groups like Conti and LockBit filling the void.
AI-Powered Attacks-
- Deepfakes on the Rise– Malicious actors are increasingly using deepfakes, AI-generated videos that mimic real people, for social engineering and disinformation campaigns. Imagine a CEO’s deepfake announcing a merger that tanks the stock market! Recent research by MIT showed deepfakes are becoming harder to detect, raising concerns about their potential misuse.
Cyber Espionage Takes Flight-
- Airline Systems Targeted- In October 2022, hackers attempted to infiltrate the IT systems of several major airlines, raising concerns about potential disruptions to flight operations and passenger data breaches. While the attacks were unsuccessful, they underscore the vulnerability of critical infrastructure to cyberattacks. (Source:)
Hope on the Horizon-
- International Collaboration- Governments and cybersecurity firms are increasingly working together to combat cyber threats. Initiatives like the Cybercrime Treaty and CISA’s Stop Ransomware.gov campaign demonstrate a growing commitment to international collaboration. (Source: )
- CISA (Cybersecurity & Infrastructure Security Agency): https://www.cisa.gov/
- FBI Cyber Division: https://www.fbi.gov/investigate/cyber
- National Institute of Standards and Technology (NIST): https://www.nist.gov/cybersecurity
- Threatpost: https://threatpost.com/
- SecurityWeek: https://www.securityweek.com/
Key Takeaways
- Cyber threats are real and evolving- – Attacks are becoming more sophisticated, utilizing AI and targeting critical infrastructure like hospitals and airlines. – Zero-day exploits and ransomware remain major threats, while deepfakes pose new challenges.
- Cyber hygiene is crucial- – Simple practices like strong passwords, software updates, and phishing awareness can significantly reduce your risk. – Consider cyber insurance for extra protection.
- International collaboration is critical- – Governments and cybersecurity firms are working together to combat cybercrime through initiatives like the Cybercrime Treaty and Stop Ransomware.gov.
- Stay informed and vigilant- – Keep yourself updated about the latest threats through reliable sources like CISA, FBI, and NIST.
Conclusion-
The digital world offers immense opportunities, but it also brings with it- cyber threats. By practicing good cyber hygiene, staying informed, and supporting international collaboration, we can build a more resilient and secure online environment for everyone. Remember: Your digital safety is in your hands. Take control and protect yourself!Frequently Asked Questions (FaQ)
What is cybersecurity?
Cybersecurity refers to the practices and technologies used to protect systems, networks, and data from digital attacks. These attacks aim to access, change, or destroy sensitive information, extort money, or disrupt normal business operations.
What is cyber resilience?
Cyber resilience goes beyond just defense and focuses on an organization’s ability to bounce back from a cyber attack. It involves preparedness, response, and recovery capabilities to minimize damage and downtime.
How to protect my business from cyber attacks?
Here are some essential steps:
- Implement strong security measures: Use firewalls, antivirus software, and data encryption.
- Educate your employees: Train them on cyber hygiene practices like using strong passwords and avoiding phishing scams.
- Patch and update software regularly: Stay ahead of known vulnerabilities.
- Have a backup plan: Ensure you can restore data and systems in case of an attack.
- Consider cyber insurance: Mitigate financial losses from cyberattacks.
4. What are Cyber Resilient and Cyber Security?
Cybersecurity focuses on preventing attacks, while cyber resilience focuses on recovering from them. Both are crucial, but resilience ensures continuity and reduces long-term impact.
What is an important digital security hack?
Use two-factor authentication (2FA) for all accounts. This adds an extra layer of protection beyond passwords.
How to protect my website from hackers and cyber attacks?
- Keep your website software updated.
- Use strong passwords and secure your hosting environment.
- Regularly scan for vulnerabilities and fix them promptly.
- Implement website security tools like web application firewalls (WAFs).
What does cyber security contain?
Cybersecurity encompasses various elements, including:
- Network security: Protects your network infrastructure from unauthorized access.
- Application security: Secures your software applications from vulnerabilities.
- Data security: Ensures the confidentiality, integrity, and availability of your data.
- Endpoint security: Protects individual devices like laptops and smartphones.
Incident response: Plan for handling and recovering from cyber attacks.
How can companies overcome cybersecurity challenges?
- Proactive approach: Invest in prevention and education, not just reaction.
- Continuous improvement: Regularly assess and update your security posture.
- Shared responsibility: Involve all employees in cyber awareness and response.
- Third-party expertise: Consider partnering with cybersecurity specialists.
What are the steps to improve corporate cyber security?
- Conduct a cybersecurity risk assessment to identify vulnerabilities.
- Develop a comprehensive security policy and procedures.
- Implement essential security controls and technologies.
- Monitor and log security activity for real-time detection.
- Regularly test and update your security posture.
Who is the best cyber security service provider in India?
Determining the “best” is subjective and depends on your specific needs. Research reputable providers with relevant expertise and certifications.
How did JPMorgan Chase cyber attack happen?
In 2014, hackers accessed millions of customer accounts through spear phishing emails. This highlights the importance of employee training and secure email practices.
Why is physical and cyber security important for companies?
Both are crucial for protecting sensitive information and assets. Physical security safeguards systems and data physically, while cyber security protects them digitally.
What is an ORP hack?
ORP (Open Redirect Protocol) vulnerabilities can be exploited to redirect users to malicious websites. Regularly updating software and web applications helps mitigate this risk.
What are some current cyber-security measures?
- Zero Trust approach: Verifying users and devices before granting access.
- Artificial intelligence (AI) and machine learning (ML) for threat detection and analysis.
- Blockchain technology for secure data storage and transactions.
What are the global implications of cyber security?
Cybersecurity concerns impact individuals, businesses, and governments worldwide. Data breaches can have economic, social, and political consequences. International cooperation is crucial to combat cybercrime and ensure a secure digital environment.




The article on cybersecurity takes a refreshing approach by framing it as “hacking your way to cyber resilience,” instilling a sense of empowerment in users. The clear and concise breakdown of essential hygiene practices, likening them to building a digital fence and maintaining a tranquil space, makes complex concepts easily graspable for all. Moreover, it doesn’t just stop at explanations; it provides actionable steps like using strong passwords and enabling multi-factor authentication. The tone throughout is positive and encouraging, highlighting the peace of mind that accompanies good cyber hygiene. It inspires readers to cultivate a flourishing online space by taking proactive steps towards security.